Cybersecurity in IIoT: your priority in a connected world
With the Industrial Internet of Things (IIoT) machine builders benefit from smart technologies. Just think of remote diagnostics, predictive maintenance and smart monitoring, as they bring efficiency and service. Yet, despite all these opportunities: what about cybersecurity? Beyond the latest regulations, it must be at the core of your IIoT strategy. Start building your digital defense now, which starts with the right mindset.

From altered control code and stolen production data to sniffer attacks and manipulated machine inputs: the threats are real and evolving. Therefore, cybersecurity is essential. While the latest regulations like the Cyber Resilience Act and NIS2 guideline provide frameworks with specific deadlines, the real value comes from embedding a security-first mindset into your everyday operations. Let's explore the key aspects of securing your IIoT environment, so you can build confidence and stay ahead of both attackers and regulatory requirements.
Understand where you are vulnerable
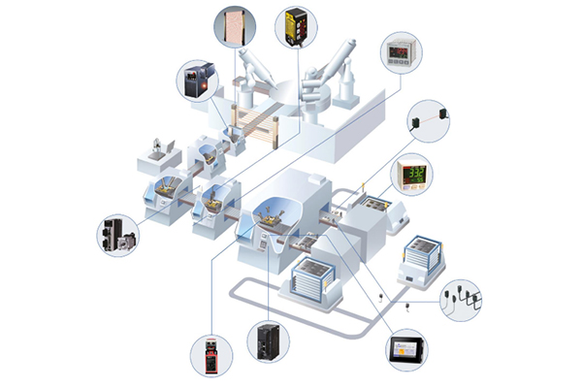
Every part of your industrial system can be targeted. Attackers may tamper with PLC control code, manipulate HMI inputs to cause unsafe machine states, or intercept data via unsecured gateways. Even something as simple as a weak password can expose critical production information. A solid cybersecurity strategy begins with a full assessment of your machine architecture, system interfaces and data flows. Understanding where your vulnerabilities lie is the foundation for building resilience.
Make cybersecurity a shared responsibility
Security must be embedded across the entire value chain. As a machine builder, your design and engineering choices directly impact system security. Operators must understand how their routines influence system resilience. A clear division of responsibilities strengthens your overall security posture and supports compliance with industrial standards.
Identify threats with the STRIDE model
To systematically uncover digital risks, think of STRIDE: Spoofing, Tampering, Reputation, Information disclosure, Denial of service, and Elevation of privilege. This approach helps identify key vulnerabilities, as it creates a concrete basis for risk mitigation across your hardware and software.
Define a practical strategy
Risk awareness is only the beginning. An effective strategy includes a segmented network architecture, strong access controls and consistent configuration management. Prioritize protection for critical components and address human factors such as weak credentials or social engineering risks. Technical issues like outdated firmware or unpatched systems must also be tackled. Clearly defined, company-wide security policies help prevent inconsistencies and make your defenses more reliable.
Monitor continuously and adjust where needed
Protecting your IIoT environment is a continuous process, not a one-time fix. It’s all about resilience and a competitive edge. Real-time monitoring, regular updates and routine testing are key to staying ahead of emerging threats. Embedding security feedback loops into daily operations ensures you're able to respond quickly and effectively to incidents, while maintaining compliance and system integrity over time.